
Terrier
Terrier is a tool designed to help law enforcement agencies (like Police) organize digital evidence, analyze packet data, and uncover critical insights making it easier to track suspicious activity and accelerate investigations.
Overview
During my tenure at Cleartrail Technologies, a cybersecurity company that builds advanced products for law enforcement and intelligence agencies worldwide, I worked on multiple projects aimed at transforming raw digital evidence into actionable intelligence.
Cleartrail’s solutions enable investigative teams to collect, process, and analyze complex communication data to solve high-stakes cases involving cybercrime, terrorism, and organized crime.
One of these projects was Terrier, a next-generation packet sniffing software designed to convert raw PCAP files into clear, legible data, helping investigators uncover patterns, connections, and critical leads during criminal investigations.
My Role
Worked as a UI/UX Designer in a cross-collaborative team, contributing to user research, persona creation, user flows, and information architecture, followed by designing the User Interface and validating it through usability testing.


Problem
Law enforcement agencies handle vast volumes of packet data that contain critical evidence, but existing analysis tools are either too technical for non-specialists or too limited for advanced investigations.
Goals
1
To create a new platform for data visualization and analytics for law enforcement agents.
2
Understand user needs and market gaps through research with investigators and analysis of existing tools.
3
Integrate multiple data sources into a single, easy-to-use interface.
4
Deliver an intuitive, secure, and efficient interface to speed up decision-making and investigations.

Approach
A user-centred, iterative approach was followed, starting with understanding the domain of communication analytics in cybercrime, then combining secondary research (literature review, law & policy study, competitor benchmarking) with primary research (interviews and surveys with law enforcement and intelligence officers). Insights from both were synthesised to uncover pain points and opportunities.
Based on these findings, concept ideation and information architecture were developed, followed by low-fidelity prototypes for early testing.
Continuous feedback from industry experts and end-users guided refinements, leading to the final design of a clean, accessible, and integrated platform tailored to real investigative workflows.
Secondary Research
I conducted secondary research by deep diving into the methodology, protocols, laws and appraoches of doing a criminal data investigation both in Indian and Global context. I interviewed Tech and Research Team for better understanding.
I conducted a competitive analysis of 10 tools, including Wireshark and NetworkMiner, to study their interfaces, workflows, and technical capabilities, and to understand how target users interact with network analysis and forensic tools.
Insights
Investigations are fragmented and protocol-heavy
Existing tools are powerful but complex
Gap between global practices and local systems
The Gap
There is no unified, intuitive, and secure platform that simplifies fragmented, highly technical workflows for law enforcement.
Primary Research
I conducted primary research by interviewing personnel from Law Enforcement and Intelligence Agencies to understand their workflows, pain points, and expectations from investigation tools. Follow-up surveys were used to capture their visual and usability preferences, which helped me identify practical challenges, user needs, and opportunities for creating a more accessible and efficient platform.
Insights
Users lack technical expertise.
Workflows are fragmented and slow.
Need for simple, visual, intuitive tools.
The Gap
there is no simple easy to learn softwares that can be used by all law enforcement agents
After gathering insights from research, we started creating personas and user journey to establish the context and usability of the application.
Persona
Depending on the responsibilities and the level of superiority, three types of personas can be created based on the age, experience, and behaviour associated with each personality type. They are:
Analyst Type A
A young Sub-constable of police with only a year of experience
is in charge of data analysis for a case investigation.
Analyst Type B
A sub-inspector with 20 years of on-field service who is given the responsibility of analyzing data for a case investigation.
Investigator
A deputy director of IB who is investigating a case and requires insights from data obtained at the scene.
.png)
Jagdish’s journey to analyze data
Scenario
Jagdish wants to capture the data files from the network of a target and compare it with the files of other suspects to get plausible connections between them. He wants to give relevant data report to his senior officer in time to help with the investigation.
Expectations
Analyze the information fast
Get desired data with a click of a button
Get print ready reports in time
Phase 1
Phase 2
Coming back and analyzing data that was captured
He comes back to office and puts all the files for analysis.
He gets various parameters of analysis and gets details on the target.
Hopeful
Excited
Enthusiastic
Phase 3
Comparing the data with a previous data file of another target
He is then asked to find any connections to a previous target.
He uploads a data file from previous records and analyzes it to extract information.
He then compares with the captured files based on parameters that were found on field
Downloading the report with suggestions and findings
Phase 4
Going to the targets place and capturing data
Jagdish sits in the same network as the target and captures all the files in that device
He discovers a few connections between them and puts auto suggestions and his own suggestions into the report.
He takes the printout of the detailed report and takes it to his team and seniors to discuss.
Anxious
Stressed
Overwhelmed
Exhausted
Agitated
Annoyed
Excited
Content
Optimistic
Use AI and ML to help with investigations
Highlight any information that can be useful.
Innovative data visualizations to help in better analysis and comparison of information.
Auto analysis to save time.
Options to add personal comments and physical discoveries.
Sharing and collaborating with teams.
Better sharing options
Digital repository of data files.
STAGES
ACTIVITIES
EMOTIONS
OPPORTUNITIES
From the persona and journey, I found users need a simple start but later require support for parallel data analysis, which shaped the tool to balance easy entry with advanced handling.
User Flow

Information Architecture

I created rough iterations through quick wireframes. I followed an elimination method by taking feedback from team members and with stakeholders.
Wireframes
.png)
.png)
.png)
.png)

.png)

Challenges
-
Understanding how to segregate and distribute information to improve user experience.
-
Designing effective filters to help users organize and access relevant information.
-
Enabling note-taking throughout the process for better tracking and context.
-
Analyzing how data is used across different contexts and adapting information distribution.
-
Balancing simplicity with complexity to meet the needs of different user groups.


Final Design
Visual Design
Identity
Font: Delight Bold

Why Terrier?
Terriers are a type of dog species that are exceptionally good at sniffing out narcotics and explosives.
They are friendly and good companions and are used by law enforcement.
Typography
Color Scheme
Neutral, Dark, High Contrast, Familiar
Heading
Mulish Semi Bold
Subheading
Mulish Medium
Body
Mulish Regular
#FFD45A
#FFFFFF
#B2B6BC
#2F3638
#1A1E1F
#000000

Components
Final Prototype
Signup/ Login

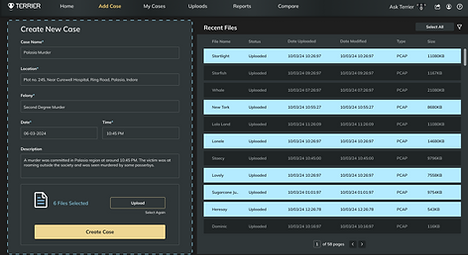
Creating a New Case
The analysis of files can only be done after creating a case. A case will contain all the details regarding the incident. To create a new case, files have to be either captured through network traffic or uploaded from archives. The case files are then processed to view detailed outcomes.

Case Contents
Once the files are processed, various parameters called Case Contents are analyzed to get to the results to the investigation.

There are a total of 12 Case Contents that can be analyzed through Terrier. Namely:
1. Location
2. IP Address
3. VoIP Calls
4. MAC Address
5. Applications
6. Devices
7. Protocols
8. Servers
9. Domains
10. Email ID
11. Phone Number
12. Media (Photos, Videos, etc)

Case Contents Interactions: Location
The case contents can be analyzed by expanding the view, Selecting a timeline, Searching through Terrier AI, Adding personal notes and Marking the results.





Case Contents Interactions: VoIP Calls
VoIP Calls can be further expand and the connections can be highlighted.

We studied Network Graphs and Ontologies to come up with visualization of VoIP Calls


Case Contents:
Media Records

Case Contents:
IP Address Records

Pattern of Life
Pattern-of-life analysis is a method of surveillence that documents or understands the habits of a person or population
Here, the pattern of life is like a comparitive analysis of all the case components in a timeline.

A single entity in the timeline can also be viewed.

Data visualization for Pattern of life was inspired by heatmaps used in interactive timeline systems.
Pattern of life can be viewed for multiple suspects.

Selected case contents can be compared.

Cross Comparison
A cross-comparison from the previous cases of parameters like Suspects, Cases or Contents can be done, and valuable insights can be brought out to ease the investigation or uncover patterns between cases.


Taking a report
After the analysis, a printed report can be generated to pass the information to a team or a superior officer. The printed report will contain a meta summary, all marked parameters with details and personal notes.


Impact
-
The product was an instant hit in the market, receiving strong validation from both industry experts and law enforcement users.
-
Helped Cleartrail position itself as a leader in intuitive cybersecurity solutions.
-
Gained real-world experience in designing a product that achieved immediate market success.
-
Learned how to translate user pain points into impactful design decisions that directly influenced adoption.



